Difference between revisions of "CTF:Writeup-Olympic-CTF-Sochi-2014"
(Write-ups for Sochi CTF 2014) |
m |
||
| Line 1: | Line 1: | ||
| − | + | = Freestyle = | |
== Freestyle 300 - Illegal Radio == | == Freestyle 300 - Illegal Radio == | ||
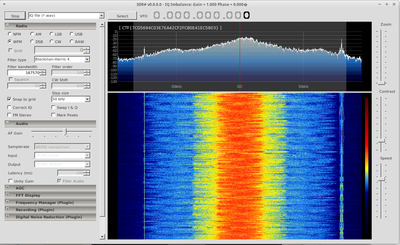
:We received a flac audio file which contained the analog recording of a digital WFM radio station. | :We received a flac audio file which contained the analog recording of a digital WFM radio station. | ||
Revision as of 01:16, 10 February 2014
Freestyle
Freestyle 300 - Illegal Radio
- We received a flac audio file which contained the analog recording of a digital WFM radio station.
- Using SDR# you we could load in a WAV file and play back the radio station.
- Command to convert flac to wav:
flac -d OLYMPIC-CTF.FM\ -\ 133.37MHz\ -\ IQ_Data.flac
- The flag was contained in the text stream that is normally displayed on the radio screen.
- SDR# can pick this information up and decode it out of the box.
Freestyle 400 - Make similar
- We received an audio recording of a fax transmission coming in.
- A large part of the problem was just finding some software that would take input from an audio file and process it as a fax. HAMFAX is able to do this but repeatedly crashed when loading the audio file. (HAMFAX only takes 8000 Hz 16 bit pcm WAV files, I converted the original .ogg file using audacity)
- I resorted to just playing the file back over a speaker and having HAMFAX decode from the microphone. This produced a fairly poor quality image but sufficient to find a section of text contained within the fax data.
- The data in the fax image turned out to be an xxencoded file plus some extra information in the form of the filesize it should be and a checksum.
- After cleaning up the image in GIMP I was able to get a reasonable OCR of the text and with some manual crosschecking got the correct checksum.
- The xxdecoded file was returned in a gzip compressed file but failed to extract the .py file it contained for some reason. Using zcat on the file rather than trying to extract it the python script (which also contained the flag) could be read.